Registration and Permissions Assignment
This section discusses the GroupID application registration and permission assignment procedure.
-
Login to Microsoft Entra Admin Center (https://portal.azure.com/) with a user that is part of the “Global Administrator” role or any role that has rights to register an app, such as the “Application administrator” role. This is required in order to give consent to certain permissions in the application.
-
In the Microsoft Entra Admin Center, go to Microsoft Entra ID > App registration and click New registration.
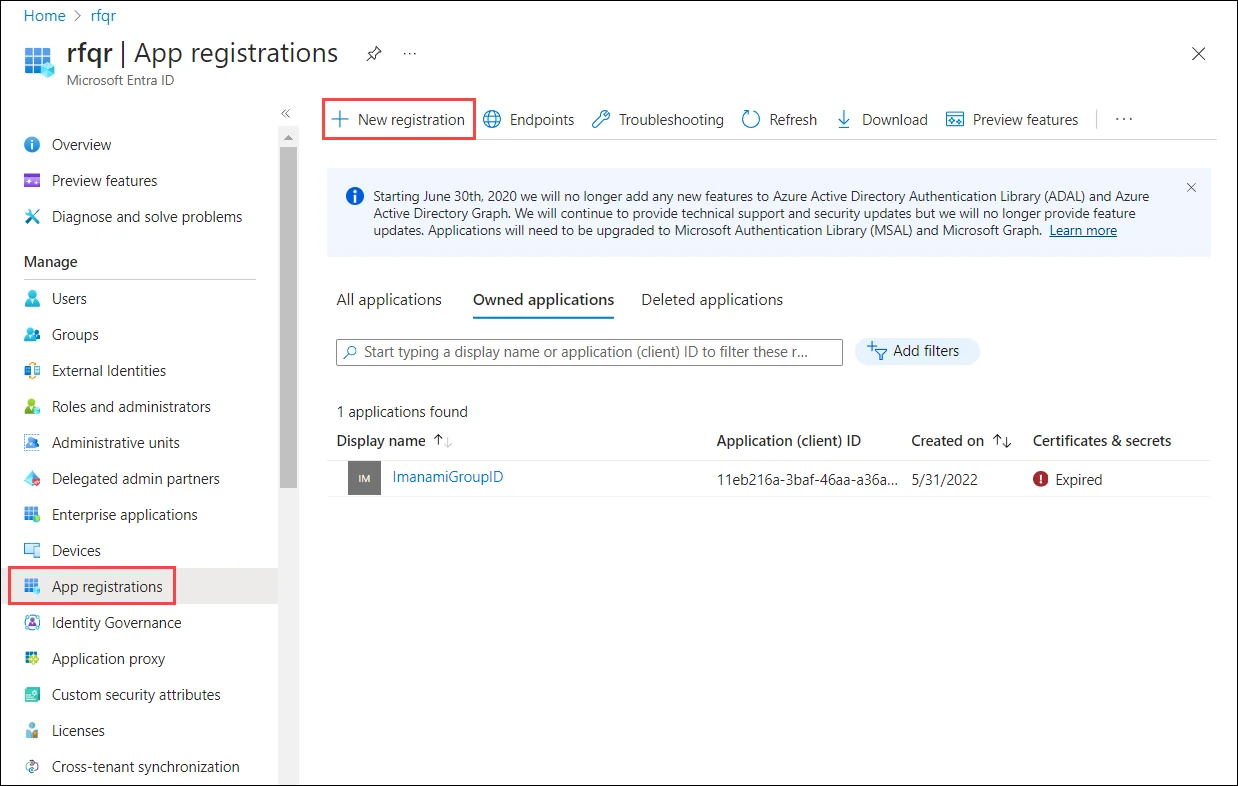
-
On the Register an application page, specify a name for the app. Select Supported account types as Accounts in any organizational directory (Any Microsoft Entra ID – Multitenant). Leave the Redirect URI as is and click Register.
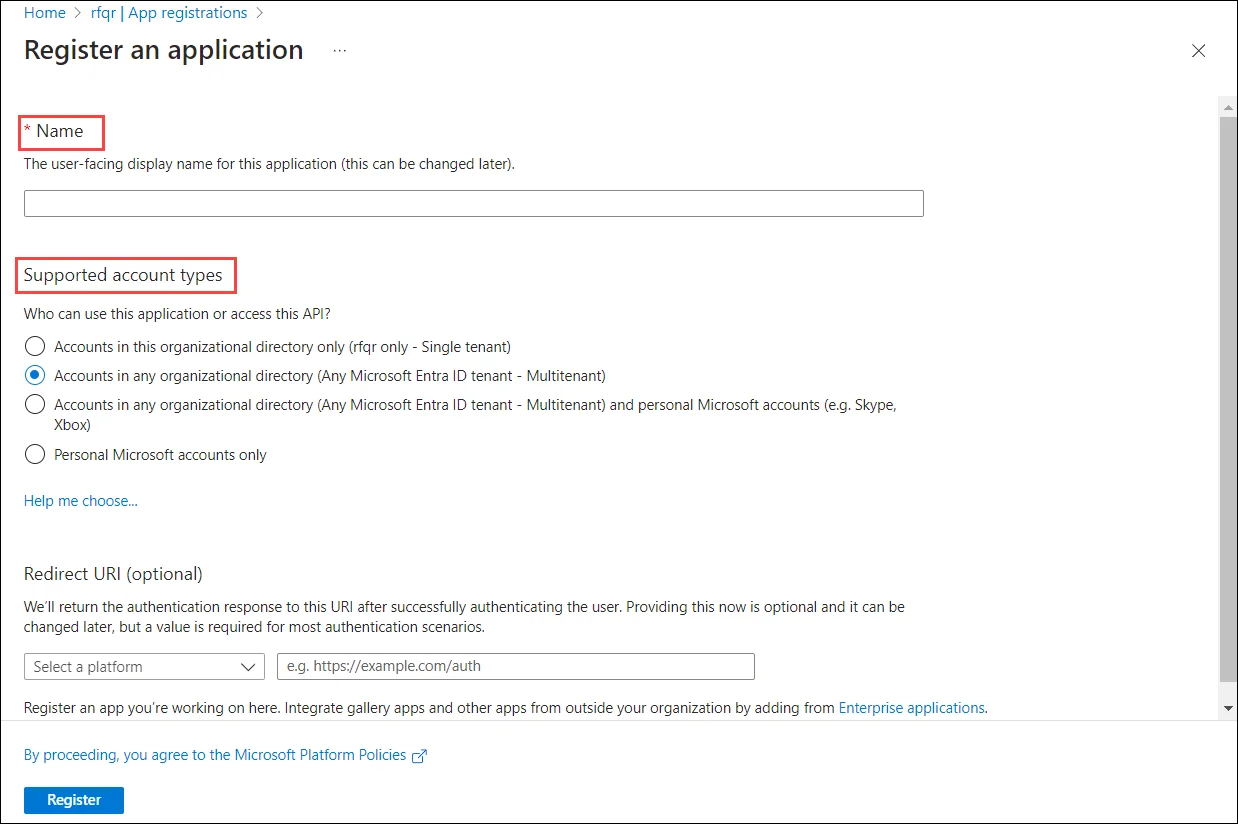
-
The Overview page is displayed. Copy the Application (client) ID and keep it safe.
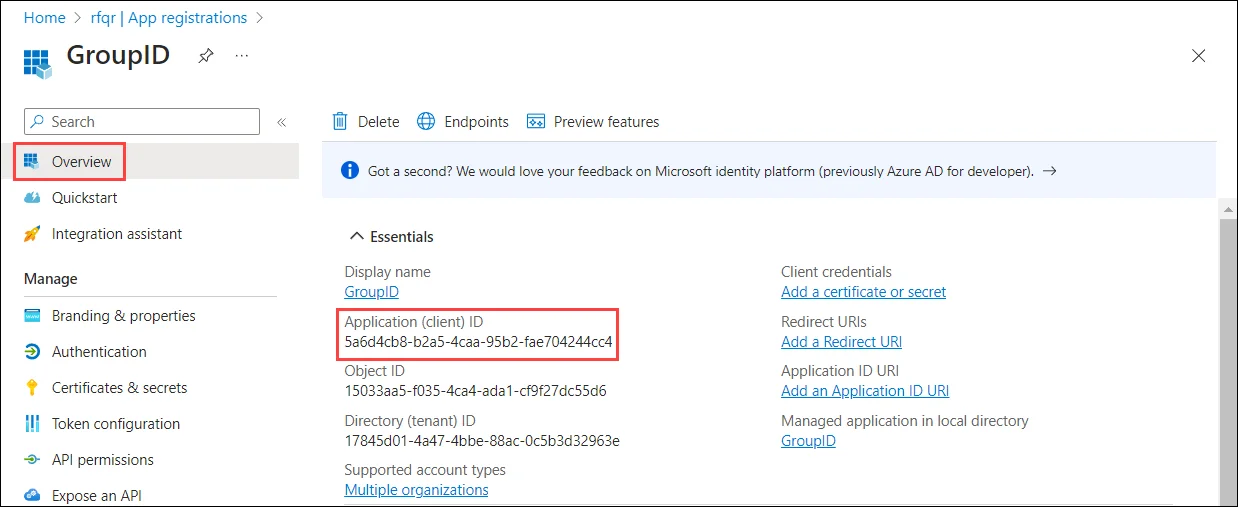
-
Go to the Authentication node and set it as follows:
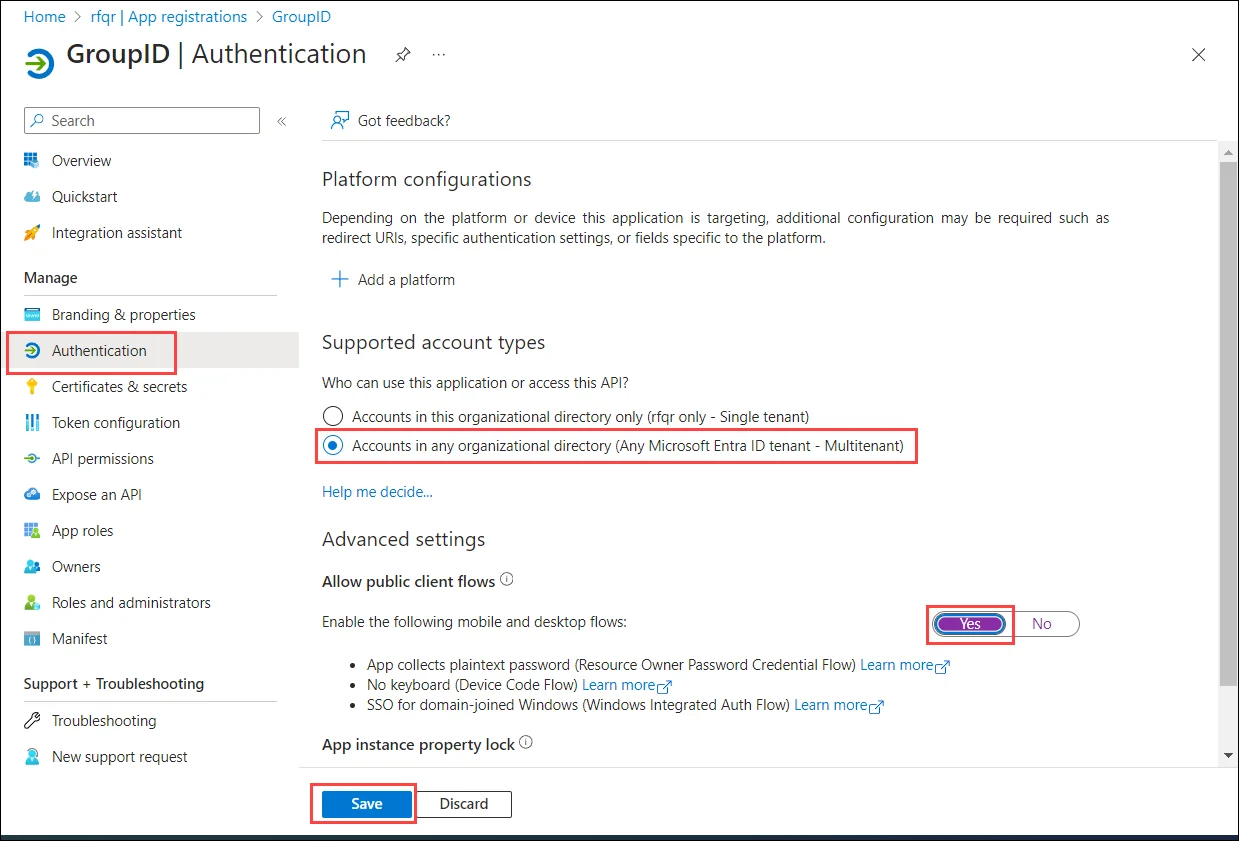
-
Click Save.
-
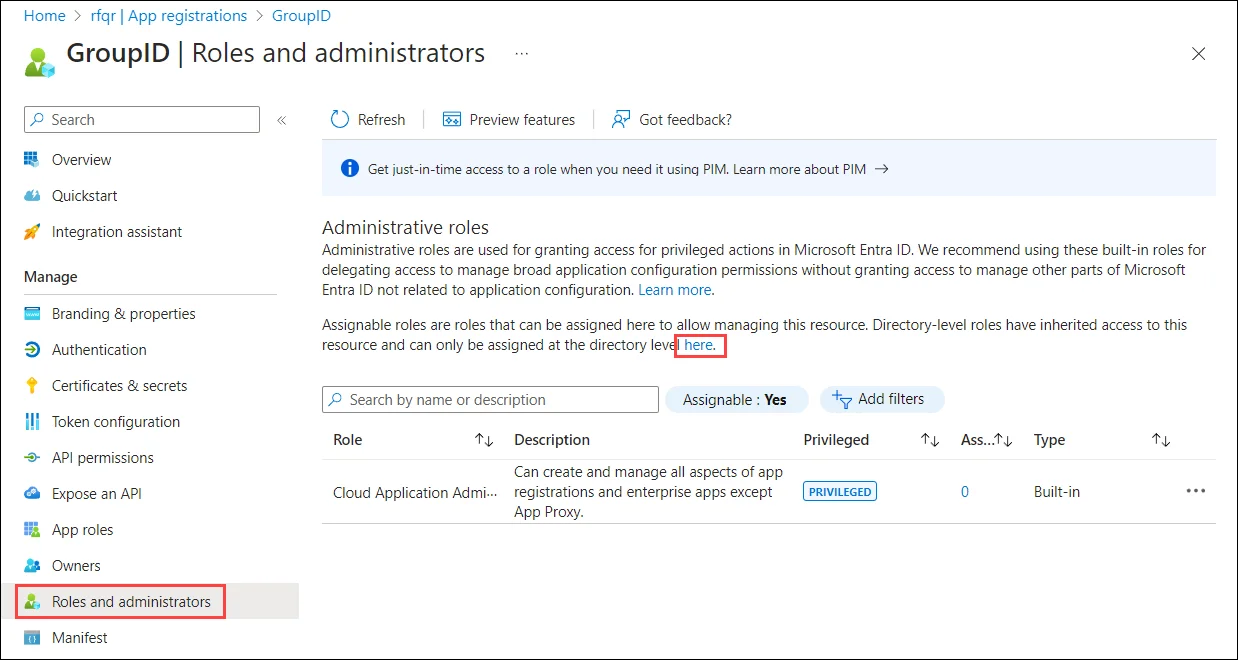
Click Roles and administrators node.
-
On the All roles page, add your registered application to a directory role.
-
Global administrator: For Global administrator, type global to filter out the Global administrator role. Click Global administrator.
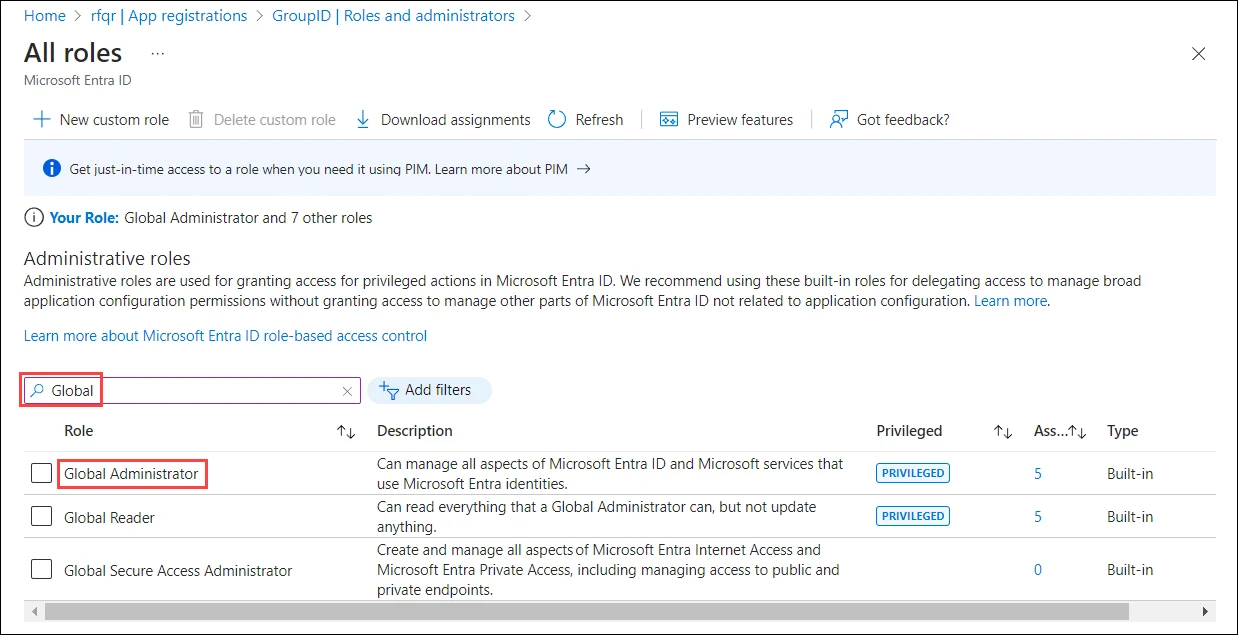
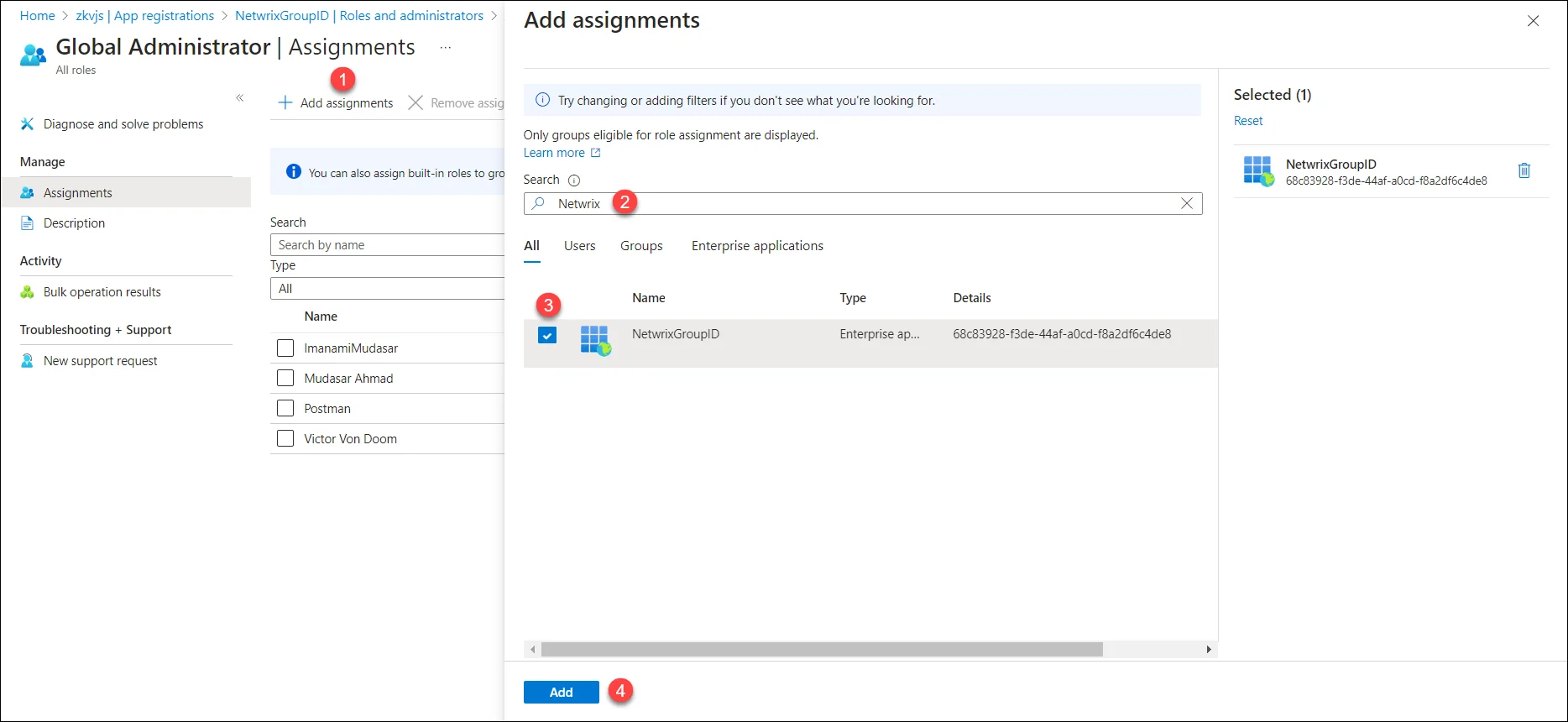
Click Add assignments. On the Add assignment page, search your application and select it. Click the Add button. The application will be listed on the Assignments page.
-
For any role other than Global administrator, add the registered application to the following two directory roles:
-
Exchange administrators: can manage all aspects of the Exchange product
-
User administrators: (User Account Administrator) can manage all aspects of users and groups, including resetting passwords for limited administrators.
For example, this role does not allow deleting a global administrator. User Account Administrators can change passwords for users, Helpdesk administrators, and other User Account Administrators only.
NOTE: By default, the GroupID Administrator security role in a Microsoft Entra IDidentity store binds to Global Administrator. If minimum role assignment for the service account is used, the default Admin Security role criteria should also be changed to the User Account Administrators group.
-
-
-
Click Add.
-
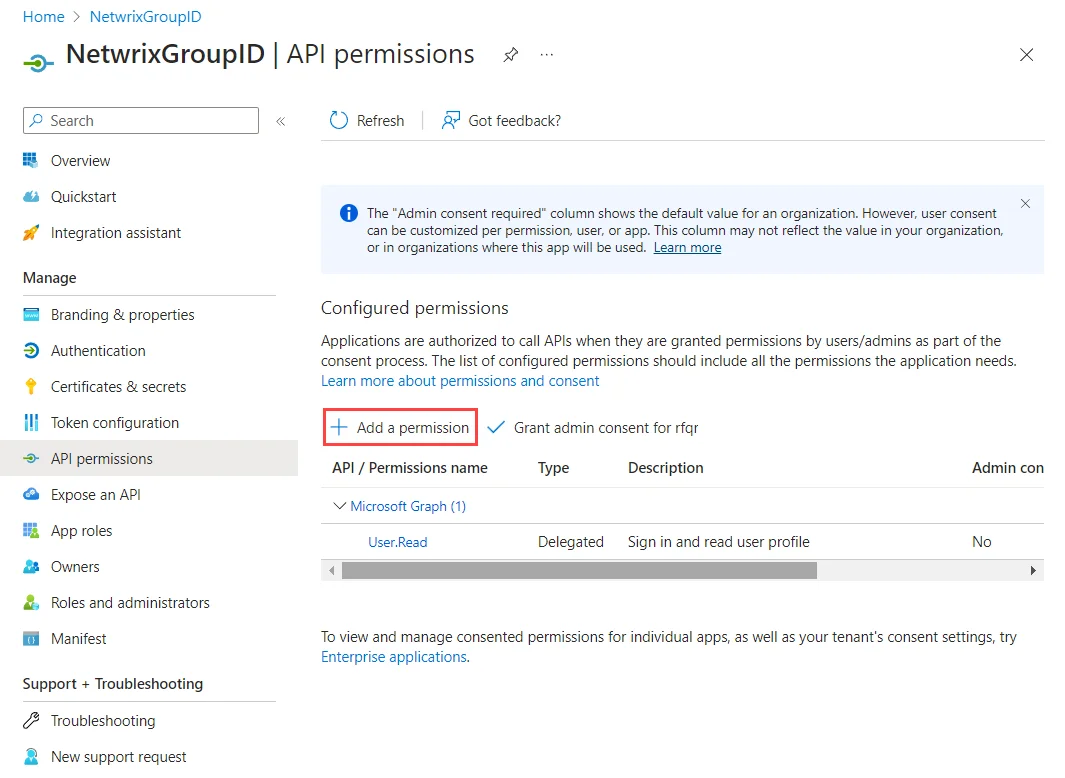
Go to the API permissions node and select Add a permission.
-
The Request API permissions page opens. Click the Microsoft Graph API tab.
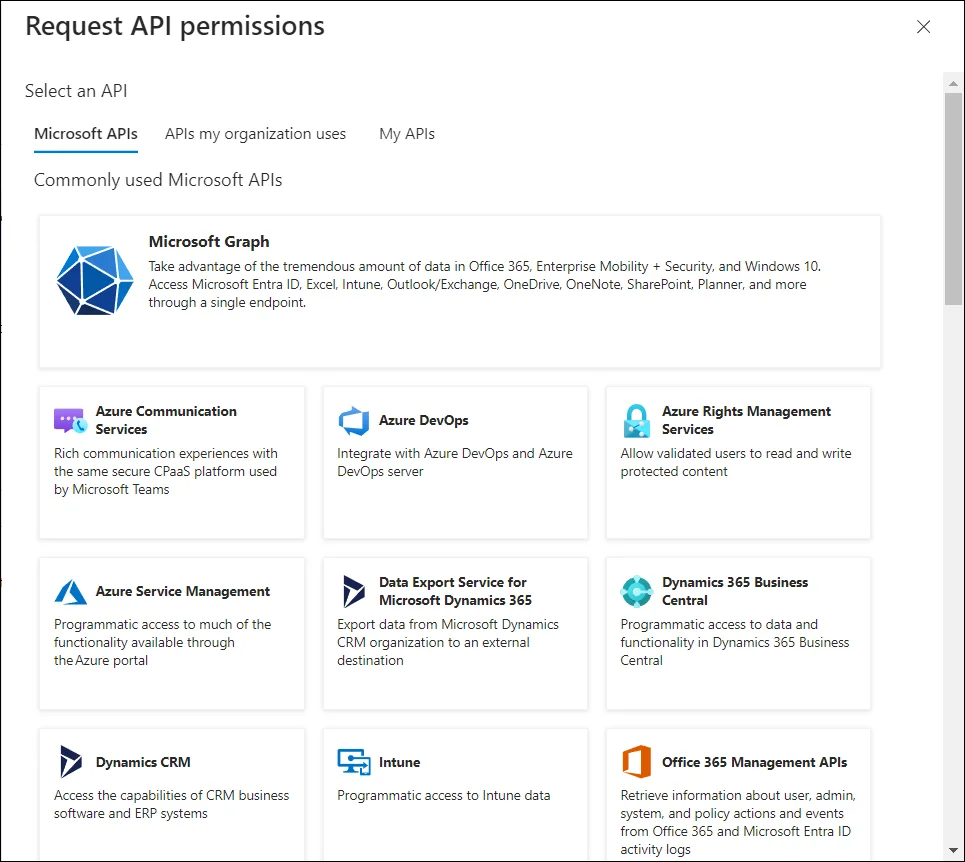
-
Click the Application permissions tab:
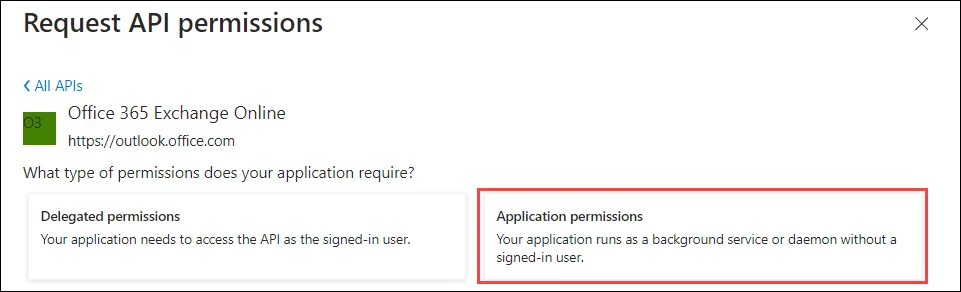
Permissions get listed on the page. See the Microsoft Entra ID Permissions topic for the mandatory permissions that are required for creating the desired directory object.
-
[Optional] To add a permission from Office 365 Exchange Online API, click the Add a permission button (before the Grant admin consent for
<username>button in the snapshot given in point # 14.Follow the steps shown on the following snapshot:
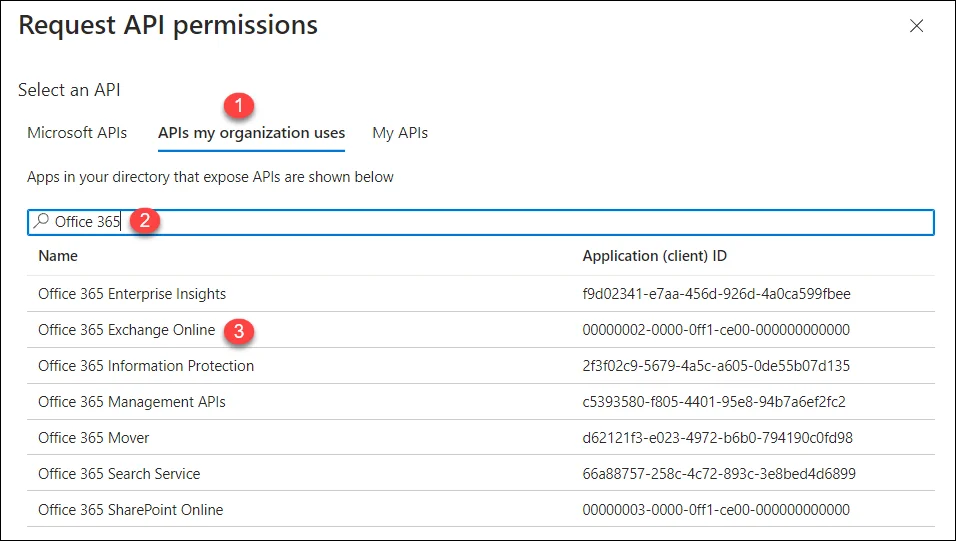
-
[Optional] To access the SharePoint API for Entitlement management, click the Add a permission button (before the Grant admin consent for
<username>button in the snapshot given in point # 14). Select the SharePoint API: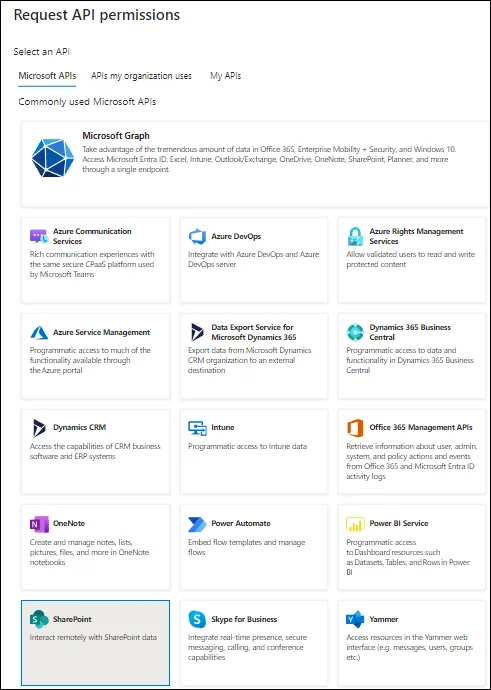
-
Select the Delegated permissions tab:
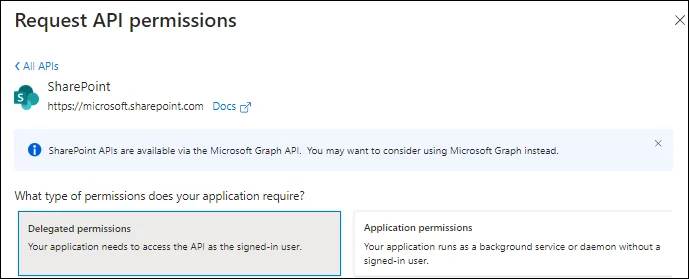
See SharePoint Delegated Permissions section of the Microsoft Entra ID Permissions topic for the required permission name.
This completes the registration process of GroupID in Microsoft Entra ID.
See Also