Active Directory
NOTE: Prior to configuring your monitoring plan, please read and complete the instructions in the following topics:
-
Protocols and Ports Required – To ensure successful data collection and activity monitoring configure necessary protocols and ports for inbound and outbound connections
-
Data Collecting Account – Configure data collecting accounts as required to audit your IT systems
-
Active Directory – Configure data source as required to be monitored
Complete the following fields:
| Option | Description |
|---|---|
| General | |
| Monitor this data source and collect activity data | Enable monitoring of the selected data source and configure Auditor to collect and store audit data. |
| Monitor Active Directory partitions | Select which of your Active Directory environment partitions you want to audit. By default, Auditor only tracks changes to the Domain partition and the Configuration partition of the audited domain. If you also want to audit changes to the Schema partition, or to disable auditing of changes to the Configuration partition, select one of the following: - Domain—Stores users, computers, groups and other objects. Updates to this partition are replicated only to domain controllers within the domain. - Configuration—Stores configuration objects for the entire forest. Updates to this partition are replicated to all domain controllers in the forest. Configuration objects store the information on sites, services, directory partitions, etc. - Schema—Stores class and attribute definitions for all existing and possible Active Directory objects. Updates to this partition are replicated to all domain controllers in the forest. You cannot disable auditing the Domain partition for changes. |
| Detect additional details | Specify additional information to include in reports and activity summaries. Select Group membershipif you want to include Group membership of the account under which the change was made. |
| Specify data collection method | You can enable network traffic compression. If enabled, a Compression Service will be automatically launched on the audited computer, collecting and prefiltering data. This significantly improves data transfer and minimizes the impact on the target computer performance. |
| Configure audit settings | You can adjust audit settings automatically. Your current audit settings will be checked on each data collection and adjusted if necessary. This method is recommended for evaluation purposes in test environments. If any conflicts are detected with your current audit settings, automatic audit configuration will not be performed. Do not select the checkbox if you want to configure audit settings manually. See the Active Directory configuration topic for additional information about audit settings required to collect comprehensive audit data and the instructions on how to configure them. |
| Collect data for state-in-time reports | Configure Auditor to store daily snapshots of your Active Directory domain configuration required for further state-in-time reports generation. See the State–In–Time Reports topic for additional information. The product updates the latest snapshot on the regular basis to keep users up-to-date on actual system state. Only the latest snapshot is available for reporting in Auditor. If you want to generate reports based on different snapshots, you must import snapshots to the Audit Database. For that, in the Manage historical snapshots section, click Manage and select the snapshots that you want to import. To import snapshots, you must be assigned the Global administrator or the Global reviewer role . Move the selected snapshots to the Snapshots available for reporting list using the arrow button. When finished, click OK. |
| Users | |
| Specify monitoring restrictions | Specify user accounts to exclude from data collection (and, therefore, search results, reports and Activity Summaries). To add a user to the exclusion list, click Add, then provide the user name in the domain\user format. Consider the following: - Use NetBIOS format for domain name: mydomain - Some audit data (events) may contain System as the user (initiator) account name. To exclude such data, specify "System" when adding a user name here. In addition to the restrictions for a monitoring plan, you can use the *.txt files to collect more granular audit data. Note that the new monitoring scope restrictions apply together with previous exclusion settings configured in the *.txt files. See the Monitoring Planstopic for additional information. |
| Objects | |
| Specify monitoring restrictions | Specify restrictions for the objects to monitor in your Active Directory. Use them to create the lists of specific objects to include and / or exclude from the monitoring scope (and, therefore, search results, reports and Activity Summaries). The following options are available: - Monitor all objects - Include these objects - Exclude these objects To create a list of inclusions / exclusions, click Add and enter object path using one of the following formats: - Canonical name, for example: mydomain.local/Computers/filesrv01 OR - Object path as shown in the "What" column of reports and search results, for example: \local\mydomain\Computers\filesrv01 You can use a wildcard (*) to replace any number of characters in the path. See the examples below for more information. |
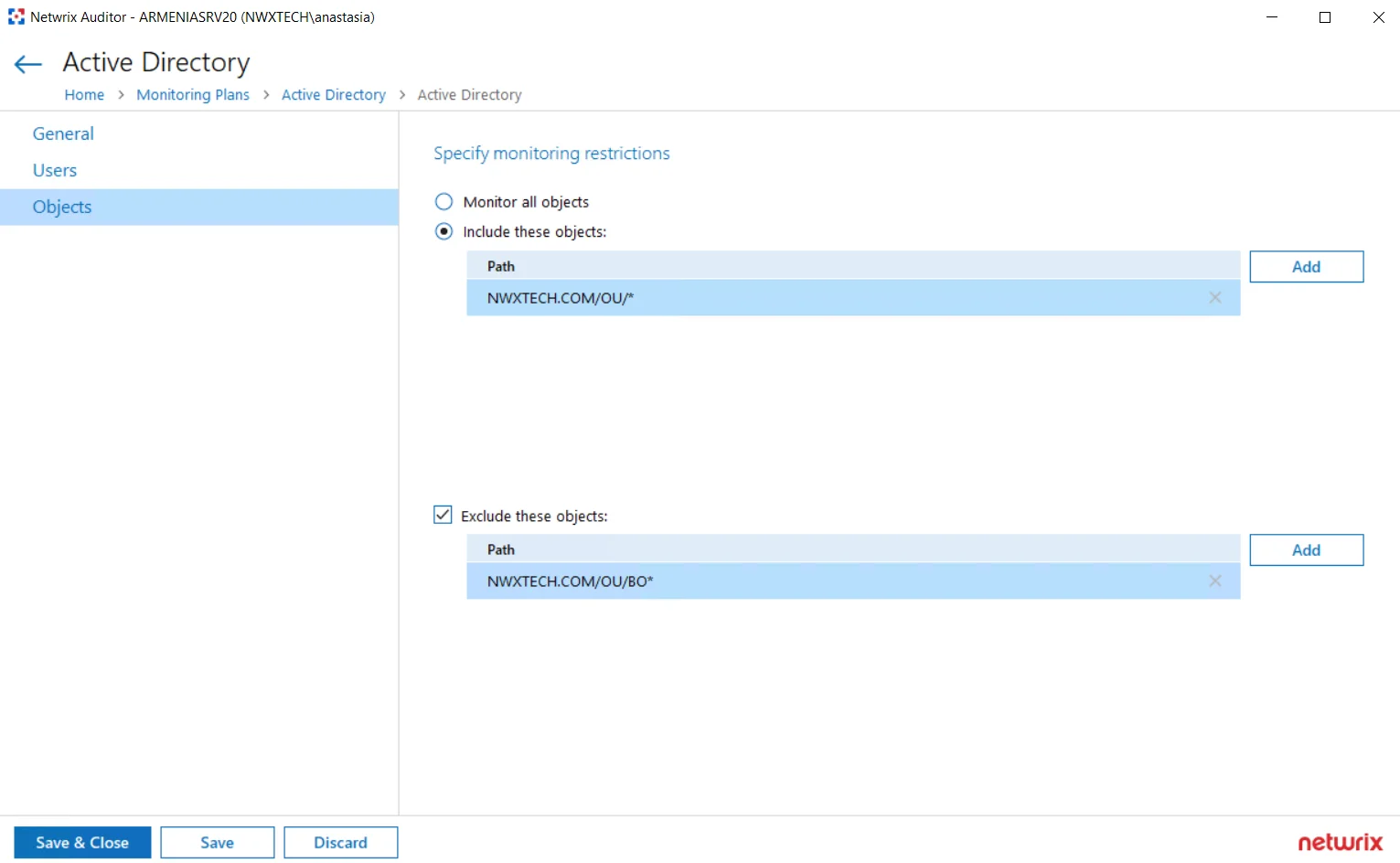
Examples
The following examples explain how the exclusion rules work. Same logic applies to the inclusion rules.
- dc11.local/OU will exclude the OU itself. However, objects within this OU will not be excluded.
- dc11.local/OU/* will exclude objects within the OU. However, the OU itself will not be excluded.
- dc11.local/OU* will exclude the OU itself, all objects within it, and also all objects whose path begins with dc11.local/OU (like dc11.local/OU_HQ).
So, with the settings as in the screenshot above, the program will monitor all objects within the OU, except for the objects whose path begins with enterprise.local/OU/BO. The OU itself, however, will not be monitored, meaning that, for example, its renaming will not be reported.
In addition to the restrictions for a monitoring plan, you can use the *.txt files to collect more granular audit data. Note that the new monitoring scope restrictions apply together with previous exclusion settings configured in the *.txt files. See the Monitoring Planstopic for additional information.
Enable Auditing of Active Directory Partitions
This topic applies to auditing Active Directory only.
Active Directory environment consists of the following directory partitions:
- Domain partition — Stores users, computers, groups and other objects. Updates to this partition are replicated only to domain controllers within the domain.
- Configuration partition — Stores configuration objects for the entire forest. Updates to this partition are replicated to all domain controllers in the forest. Configuration objects store the information on sites, services, directory partitions, etc.
- Schema partition — Stores class and attribute definitions for all existing and possible Active Directory objects. Updates to this partition are replicated to all domain controllers in the forest.
By default, Netwrix Auditor only tracks changes to the Domain partition and the Configuration partition of the audited domain. If you also want to audit changes to the Schema partition, or to disable auditing of changes to the Configuration partition do the following:
You cannot disable auditing the Domain partition for changes.
To enable auditing of the Configuration and Schema partitions
- Navigate to All monitoring plans > your monitoring plan > Active Directory.
- In the right pane, click Configure, next to Advanced Options.
- In the Advanced Options dialog, select Configuration and Schema.
Information on changes to the selected partitions will be available in reports and will be saved in snapshots.
AD Container
Complete the following fields:
| Option | Description |
|---|---|
| General | |
| Specify AD container | Specify a whole AD domain, OU or container. Click Browse to select from the list of containers in your network. You can also: - Select a particular computer type to be audited within the chosen AD container: Domain controllers, Servers (excluding domain controllers), or Workstations. - Click Exclude to specify AD domains, OUs, and containers you do not want to audit. In the Exclude Containers dialog, click Add and specify an object. The list of containers does not include child domains of trusted domains. Use other options (Computer, IP range to specify the target computers. |
| Specify the account for collecting data | Select the account that will be used to collect data for this item. If you want to use a specific account (other than the one you specified during monitoring plan creation), select Custom account and enter credentials. The credentials are case sensitive. Starting with version 9.96, you can use group Managed Service Accounts (gMSA) as data collecting accounts. If using a group Managed Service Account, you can specify only the account name in the domain\account$ format. Password field can be empty. A custom account must be granted the same permissions and access rights as the default account used for data collection. See theData Collecting Account topic for additional information. |
| Containers and Computers | |
| Monitor hidden shares | By default, Auditor will monitor all shares stored in the specified location, except for hidden shares (both default and user-defined). Select Monitor user-defined hidden shares if necessary. Even when this option is selected, the product will not collect data from administrative hidden shares such as: default system root or Windows directory (ADMIN$), default drive shares (D$, E$, etc.), shares used by printers to enable remote administration (PRINT$), etc. |
| Specify monitoring restrictions | Specify restriction filters to narrow your monitoring scope (search results, reports and Activity Summaries). All filters are applied using AND logic. Depending on the type of the object you want to exclude, select one of the following: - Add AD Container – Browse for a container to be excluded from being audited. You can select a whole AD domain, OU or container. - Add Computer – Provide the name of the computer you want to exclude as shown in the "Where" column of reports and Activity Summaries. For example, backupsrv01.mydomain.local. Wildcards (*) are not supported. In addition to the restrictions for a monitoring plan, you can use the *.txt files to collect more granular audit data. Note that the new monitoring scope restrictions apply together with previous exclusion settings configured in the *.txt files. See the Monitoring Planstopic for additional information. |
Domain
Complete the following fields:
| Option | Description |
|---|---|
| Specify Active Directory domain | Specify the audited domain name in the FQDN format. For example, "company.local". |
| Specify the account for collecting data | Select the account that will be used to collect data for this item. If you want to use a specific account (other than the one you specified during monitoring plan creation), select Custom account and enter credentials. The credentials are case sensitive. You can also use group Managed Service Accounts (gMSA) as data collecting accounts. If using a Managed Service Account, you can specify only the account name in the domain\account$ format. Password field can be empty. A custom account must be granted the same permissions and access rights as the default account used for data collection. |
See the Permissions for Active Directory Auditing topic for additional information.